The Department of Homeland Security released a list of cybersecurity performance goals and metrics designed by the Cybersecurity & Infrastructure Security Agency (CISA) to help drive cybersecurity best practices across the private sector.
What is the CISA?
The CISA works daily with government, private sector, and international partners to gain unique insights into cybersecurity across the US.
The Cross-Sector Cybersecurity Performance Goals document includes a list of best practices for securing accounts, devices, and data, vulnerability management, governance, the supply chain, and recovery. This list of cybersecurity good practices comes in answer to the fact that there are still significant gaps in the National Cybersecurity landscape:
1. Most organizations don't have fundamental security protections.
Lacking foundational measures and basic protections such as multi-factor authentication (MFA), strong password management, and backups exposes organizations to cyber intrusions.
2. Small- and medium-sized organizations are struggling to keep up.
Primarily because of limited resources, they often need help knowing where to start to protect themselves in reasonable and sustainable ways.
3. Inconsistent cybersecurity standards across different sectors and overlooked operational technology-related risks.
Organizations have been ignoring operational technology as a rising attack surface, and cybersecurity standards across different sectors need to be more consistent or better.
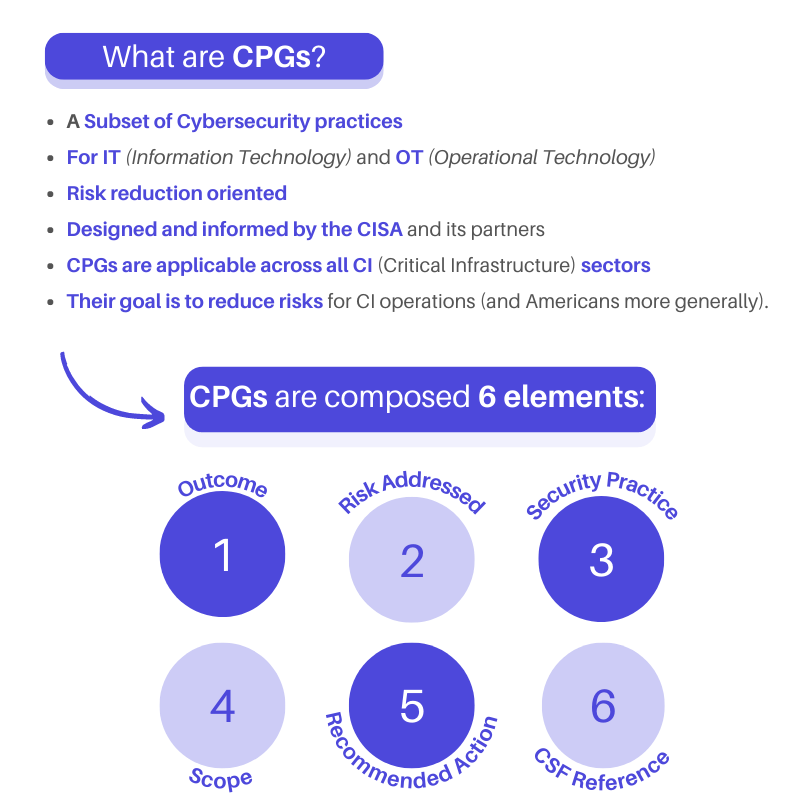
WHAT ARE THE CPGs?
The CISA puts it this way "the CPGs are a prioritized subset of IT and OT cybersecurity practices aimed at meaningfully reducing risks to both CI operations and the American people." CPGs are divided into eight sections: Account Security, Device Security, Data Security, Governance and Training, Vulnerability Management, Supply Chain / Third Party, Response and Recovery, and Others.
Here is an example from the Cross-Sector Cybersecurity Performance Goals Report:
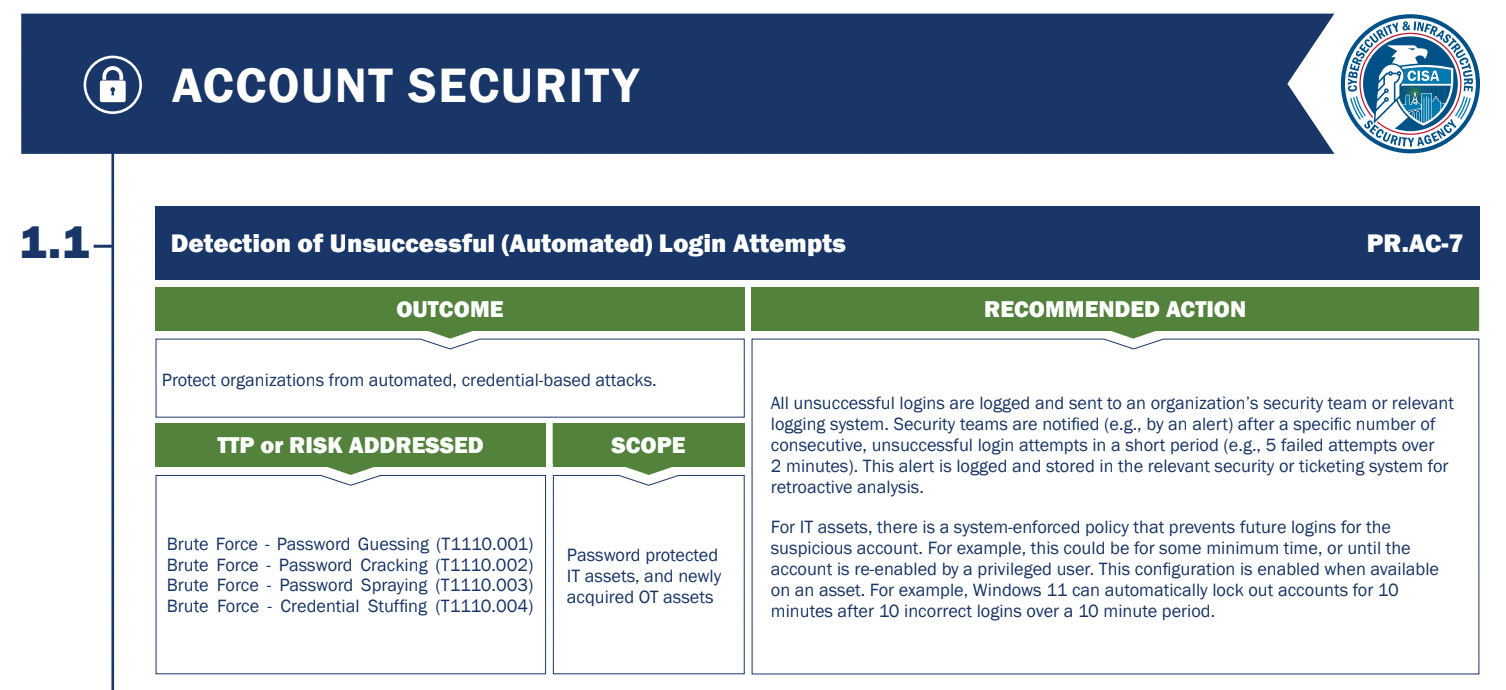
Credit: CISA
How to apply them to your organization?
The CISA's document includes a "user-friendly" worksheet to clarify and facilitate your cybersecurity strategy. However, as it can be difficult for Organizations to know where to start and how to allocate resources, a good alternative is to work with an MSP (Managed Services Provider), who can ensure your cybersecurity strategy and deployment is on point.
Should you work with an MSP for your cybersecurity? Here are five benefits this decision could bring to your organization:
- A team of experts: with knowledge in multiple areas.
- In-depth reporting: MSPs are proactive; they report any areas that can be improved or could cause future problems.
- Peace of mind: the rising of cyber attacks became most organizations' worry when they could let professionals take care of it.
- Transparent pricing: allows organizations to predict ongoing costs and integrate them into their financial strategy.
- Available support whenever you need it: when choosing an MSP, ensure they cover the entire US timezone and provide on-site support and a remote helpdesk.
Book a free cybersecurity audit to make the right decision for your organization.