The convenience of public Wi-Fi networks comes with hidden risks that could compromise your business's sensitive data. While these networks offer seamless connectivity in coffee shops, airports, and hotels, they also present significant security vulnerabilities that cybercriminals actively exploit.
Understanding Modern Wi-Fi Security Threats
Understanding these threats is crucial for protecting your business assets. Two particularly sophisticated attack methods - Man-in-the-Middle (MITM) and Evil Twin attacks - pose serious risks to organizations whose employees regularly use public Wi-Fi networks.
Consider a typical scenario: A business executive connects to a coffee shop's Wi-Fi network to check company emails and access financial records. Unknown to them, a cybercriminal has positioned themselves between their device and the network through a Man-in-the-Middle attack. This invisible interceptor can now monitor all transmitted data, including passwords, confidential emails, and financial information. The breach often goes undetected until significant damage has already occurred.
Evil Twin attacks represent an equally concerning threat. Cybercriminals create counterfeit networks that mimic legitimate ones - for instance, setting up "Airport_Secure_WiFi" alongside the official "Airport_WiFi."
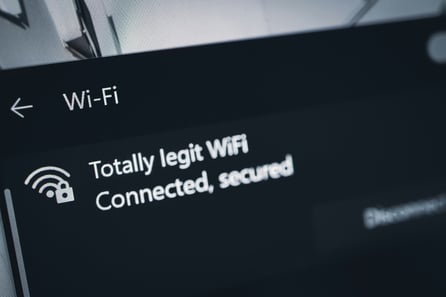
Once a user connects to these deceptive networks, attackers can harvest login credentials, steal authentication cookies, and even deploy malware directly to connected devices. The implications for businesses extend beyond immediate data theft to potential long-term security compromises.
Essential Security Measures for Business Protection
These threats may seem overwhelming, but implementing robust security measures can significantly reduce your risk exposure. Here are seven essential protective strategies for your business:
- Establish Data Handling Protocols
Implement strict guidelines for sensitive information management. Reserve activities involving confidential data, such as accessing financial accounts or conducting secure transactions, for trusted networks only. Treat public Wi-Fi as a shared space where others might be monitoring your activities.
- Verify Website Security
Ensure all business-related sites use HTTPS encryption. Look for the padlock icon in your browser's address bar, indicating a secure connection. This fundamental step provides an essential layer of protection for your data transmission.
- Deploy Security Extensions
Install and maintain security-focused browser extensions to enhance your defense against potential threats. These tools can effectively block malicious content, manage cookies, and alert users to suspicious websites before any damage occurs.
- Manage Network Connections
Disable automatic network connections on all business devices. This simple configuration change prevents devices from connecting to potentially dangerous networks without explicit authorization, reducing the risk of inadvertent exposure.
- Implement Pop-up Protection
Train employees to recognize and avoid suspicious pop-ups, which often serve as entry points for malware and phishing attempts. A single misclick can compromise an entire network's security, making awareness crucial.
- Enable Two-Factor Authentication
Implement two-factor authentication across all business applications. This additional security layer significantly reduces the risk of unauthorized access, even if credentials become compromised through public Wi-Fi attacks.
- Maintain Regular Updates
Establish rigorous software update schedules. Regular updates patch security vulnerabilities and strengthen your defense against emerging threats. Consider automating this process to ensure consistent protection across all business devices.
Advanced Protection Strategies
Beyond these essential measures, businesses should consider implementing advanced security protocols such as:
- Virtual Private Networks (VPNs) - Deploy enterprise-grade VPN solutions for all remote workers, ensuring encrypted connections regardless of the network being used.
- Mobile Device Management (MDM) - Implement MDM solutions to maintain control over business devices and enforce security policies automatically.
- Security Awareness Training - Conduct regular training sessions to keep employees updated on the latest security threats and best practices for public Wi-Fi usage.
The landscape of cybersecurity threats continues to evolve, making vigilance in protecting business data increasingly important. While public Wi-Fi networks offer undeniable convenience, their benefits must be weighed against potential security risks.
Our team specializes in developing comprehensive security solutions tailored to your business needs. Contact us to learn how we can help protect your sensitive data across all networks, ensuring your business maintains both connectivity and security in today's mobile work environment.