Anchore's study found that software supply chain attacks impacted 62% of organizations. A global survey of 1,000 CIOs indicated that 82% say their organizations are vulnerable to cyberattacks that target software supply chains.
What is a "software supply chain attack"?
A software supply chain attack (also called a third-party attack, backdoor breach, or even value-chain attack) occurs before a vendor sends the software to its client: a malicious actor infiltrates a software vendor's network and compromises it, to access a business's network. They are even more challenging to detect and prevent if your vendors aren't maintaining strict cybersecurity policies and using the best tools.
Example of a software supply chain attack: a keylogger (spyware that can record and steal consecutive keystrokes that a user enters on a device) placed on a USB drive can make its way into a large retail company, which then logs keystrokes to determine passwords to specific accounts. Cybercriminals can access sensitive company information, customer records, payment information, and more.
This type of cyber attack requires only one compromised application or piece of code to affect the entire supply chain. Repercussions can be very damaging for businesses. The recent SolarWinds attack is a prime example.
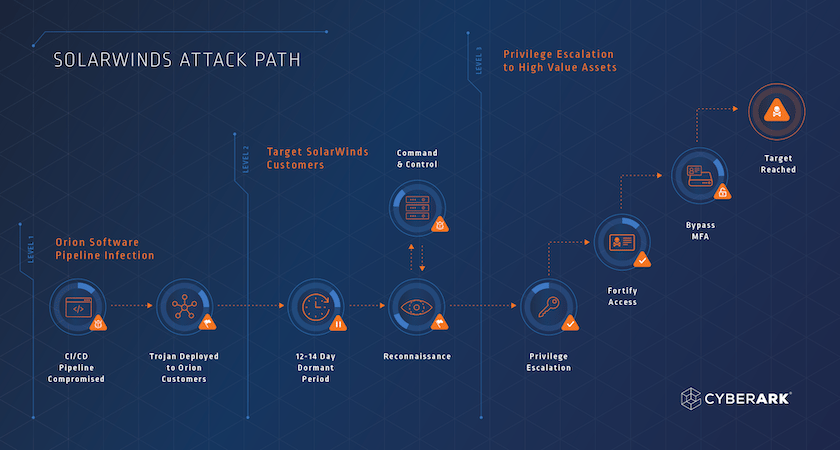
Nowadays, businesses are more connected than ever: the software supply chain is neither linear nor simplistic. Systems are often massive in scope and quite complex in terms of relationships. This setup makes it very hard to detect and trace cyber attacks, and as organizations hasten software development cycles to remain competitive, security breaches are becoming a critical issue for businesses. Unfortunately, most of the time, developers don't have time to find and fix them.
.png?width=840&name=Sans%20titre%20(8).png)
What are the three most common software supply chain attacks?
1. Hijacking updates
It consists in inserting malware into the outgoing update or altering the update. The objective is to grant the threat actor control over the software's normal functionality.
2. Undermining code signing
Threat actors hijack software updates by impersonating a trusted vendor and inserting malicious code into an update.
3. Compromising open-source code
This attack refers to when threat actors insert malicious code into publicly accessible code libraries.
It is essential to know that these techniques are not mutually exclusive, and threat actors often leverage them simultaneously.
What can organizations do to minimize software supply chain attacks?
1. Invest in SOC (security operation center) analysts.
Outsourced IT support can help you monitor your business's cybersecurity infrastructure and identify any problems or potential breaches.
2. Simulate a fake software supply chain attack.
This technique will help you see whether your cybersecurity is enough and how the systems react to attacks.
3. Have contingency plans which include every third-party provider.
As said above, supply chains are getting more and more complex, involving a multitude of actors. Preparing your company against cyber attacks on any of your supply chain elements/partners is essential.
4. Restrict vendors' access.
It is an excellent way to mitigate potential threats since vendors will only be able to access what they need for the job.
Cybersecurity issues can be quite overwhelming and very time-consuming. At LENET, our mission is to help and guide organizations through their digitalization while ensuring their maximum security. Don't hesitate to reach out.